We support you in selecting, collecting and storing your security relevant logs to enable security monitoring for effective detection and prevention of security incidents.
When deciding to install a SIEM in your company, several questions arise: what will the Log Management do, how shall it be integrated into your existing IT-Infrastructure and how can it be used for various branches of your business?
Log Management is not just collecting logs, or creating and analyzing alarms and reports. The process of Log Management is much more complex. It requires huge amounts of knowledge, human brainpowerand time.
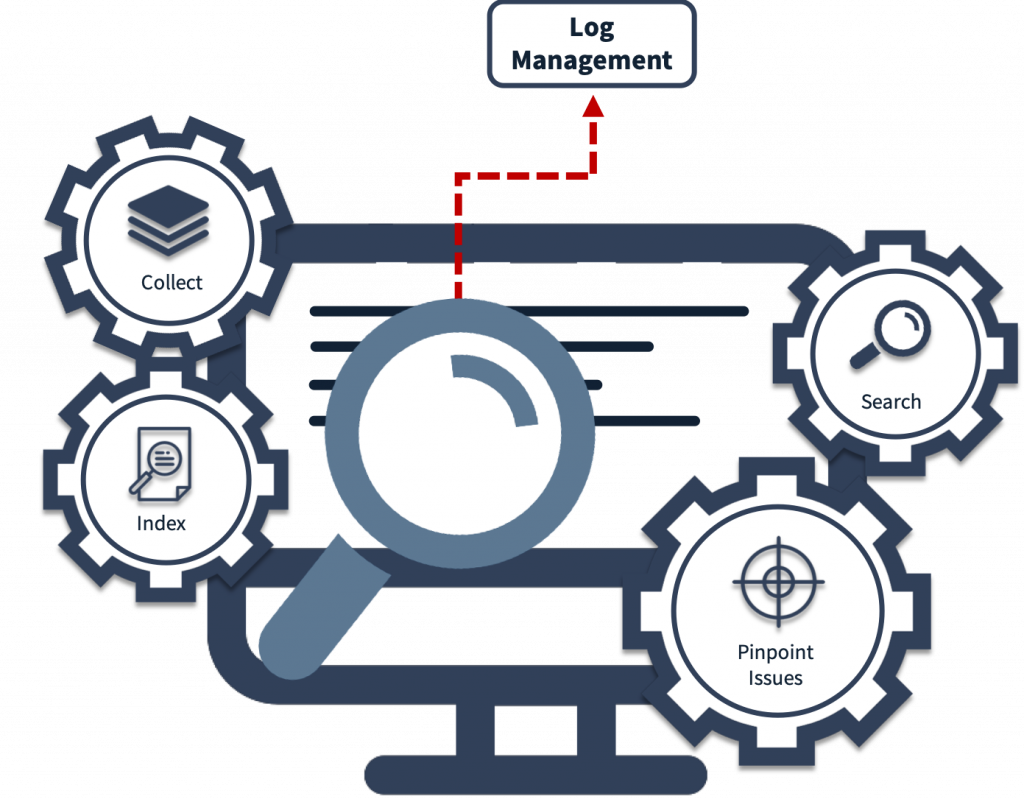
Log Management consists of at least seven main components:
1. Log File Collection: the collection of all relevant and necessary Log Files.
2. Parsing: collected logs come from different operating systems, applications, firewalls, proxy servers and more in totally different structures. Parsing breaks them down into smaller processable elements for with a dedicated meaning for further usage and processing.
3. Normalization: the process of normalization aligns fields and scales within parsed logs coming from different sources which have the same meaning, but are scaled differently or use synonyms for the represented value. Normalizing them they enables source agnostic searches and processing.
4. Indexing: indexing stores whole log lines or references in specialized dictionaries. This enables drastically enhanced search speeds within large data sets.
5. Correlation: describes the process of linking whole log lines or specific fields with information in other data sets. These data sets can be simple lookup tables or logs from different sources. This enrichment can make the logs easier understand, e.g. by linking the MAC-address-field with a CSV-file containing the related hostnames, or provides a different view on the information within the data set, e.g. false positive and false negative reduction.
6. Search and Analysis: finding relevant events of interest to your business for security or compliance reasons (for example, building searches that only cover relevant events regarding the amount of data, false positives and limited storage).
7. Reports, Dashboards and Alarming: setting up the right forms of analysis, searches, alarms and reports is an agile, complex and elaborate process. Making the right choice is also complexand user requirements change quickly.
By using our Managed Log File Management you will be sure of making each of these essential steps and you will avoid the risk of overlooking essential compliance and security guidelines for your company.
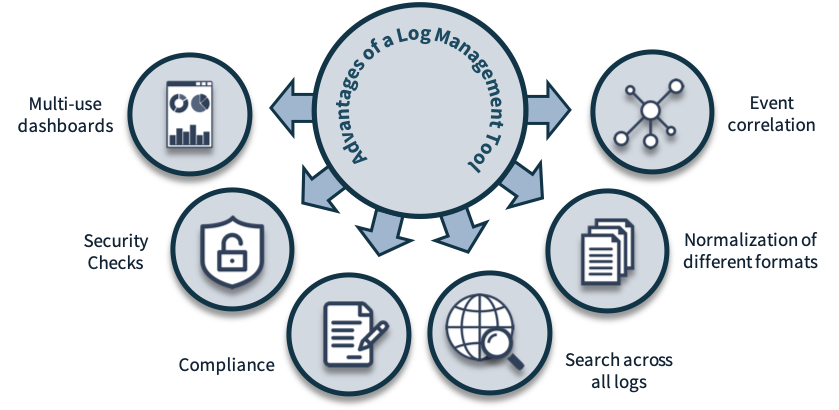
We support you in selecting, collecting and storing your security relevant logs to enable security monitoring for effective detection and prevention of security incidents.
We ensure your end to end user audit trail and regulatory compliance and offer both on site support and managed services.
