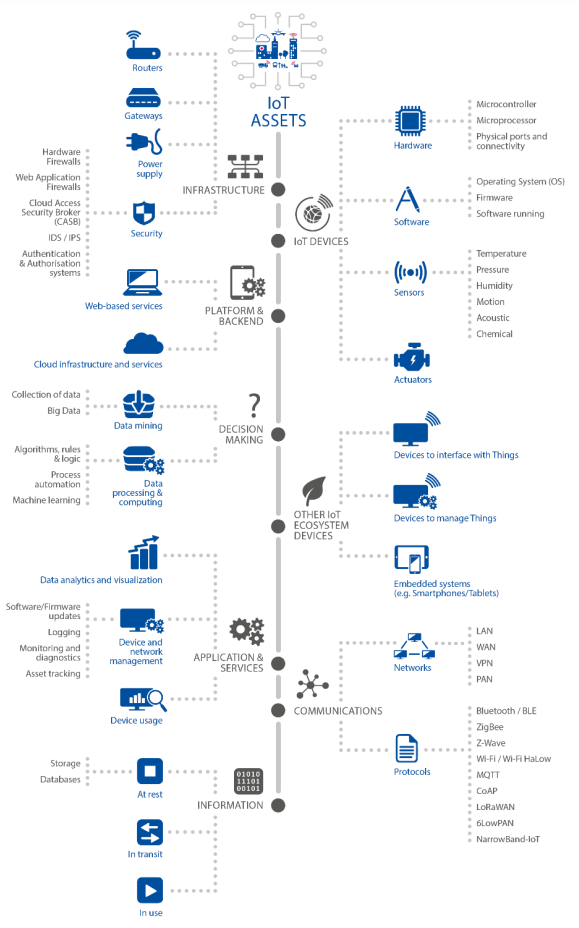
The Internet of Things (IoT) describes a fully connected world with on-demand access to information and systems that process this information. It includes all intelligent, interconnected objects imaginable – billions of them – like sensors in cars, TV’s, or washing machines (refer to figure 1). This level of connectivity and amount of data generated and transferred brings new risks towards the security goals integrity, confidentiality, and availability of the devices and networks involved [1,2].
The attack surface increases
In a comprehensive study, ENISA has uncovered several risks coming with IoT [3]. The main risks for corporations are:
- Existing mitigation measures might not be applicable to IoT devices as they often come with technical constraints, limited capabilities, and limited resources.
- The low cost usually associated with IoT devices might have an impact on their security, for example, by limiting security features, or prioritizing functionality over secure programming.
- By deploying IoT on top of legacy systems, critical infrastructures are “becoming smart”.
- Lack of expertise in IoT security combined with the lack of traditional update mechanisms in IoT devices.
According to the study, data leakage, weak passwords, malware, exploits, and DDoS are the threats with the highest impact on IoT.
An organization should secure against these threats with a combination of organizational and technical measures.
Security and Privacy by design
The IoT system and its integration should be designed in a holistic approach. The architecture should be encapsuled by use case, process or department. Privacy must be an integral part of this design and checked with impact assessments.
Adapt your processes to include IoT
An organizations life cycle management process for assets should take IoT assets into account and the asset inventory should include all IoT assets, including their location and life cycle status. This will support the vulnerability and patch management process which must also be extended to include IoT.
New contracts with suppliers, contractors, and other third parties should include RACIs related to the functions provided; existing relationships should be updated accordingly. Organizations should consider the whole IoT supply chain when it comes to information security [4].
Awareness training for employees should be extended to train about roles and responsibilities as well as privacy and security practices related to IoT.
Secure IoT with technical measures
Organizations should only use IoT that incorporates security features. Applicable security features should be enabled by default and all unused functionality should be disabled. Default passwords should be changed immediately.
The actions allowed on a device should be limited to the use case, for example, by applying a role-based access model.
Communication with the device and its network services should be secured by cryptographic measures and network segmentation.
More technical measures can be found within ENISAs Baseline Security Recommendations for IoT in the context of Critical Information Infrastructures [3] and the Guidelines for securing the internet of things [4].
Recommendation
Check if your organization`s IoT assets are secured properly:
- Are your processes and procedures harmonized to incorporate your IoT into the IT?
- Do your awareness programs include IoT risks?
- Does a clear responsibility and accountability for an IoT strategy and its implementation exist?
Need help securing the IoT assets of your organization? Contact us for more information.
Sources
- [1] https://www.nist.gov/internet-things-iot
- [2] https://www.bakom.admin.ch/bakom/en/homepage/digital-switzerland-and-internet/internet/internet-of-things.html
- [3] https://www.enisa.europa.eu/publications/baseline-security-recommendations-for-iot
- [4] https://www.enisa.europa.eu/publications/guidelines-for-securing-the-internet-of-things
