Ransomware is one of today’s much discussed types of cyber attack. Several business models around this attack type emerged during the last years. The schema boils down to a threat actor using malware to take control over personal or organizational assets with the aim of demanding ransom. That way threat actors seem to successfully target availability and confidentiality of the business values of many organizations around the globe. In fact, ENISAs recent threat landscape report on ransomware attacks states that employees’ personal data was included in more than 50% of data stolen in these kinds of attacks during the last year [1].
Organizations of every Size and from all Sectors are Affected
According to ENISA, Germany ranks #2 and Switzerland ranks #7 when it comes to the countries with the highest number of registered ransomware incidents. Heavy industry, information services and government are the top three sectors targeted.
ENISA also states that organizations are often not aware of the attack path, especially how the initial access to the organization was achieved by the threat actors. But initial access is just the start of such an attack. The federal office for information security explains which proactive and reactive measures can help organizations in every phase of the Ransomware Killchain [2]:
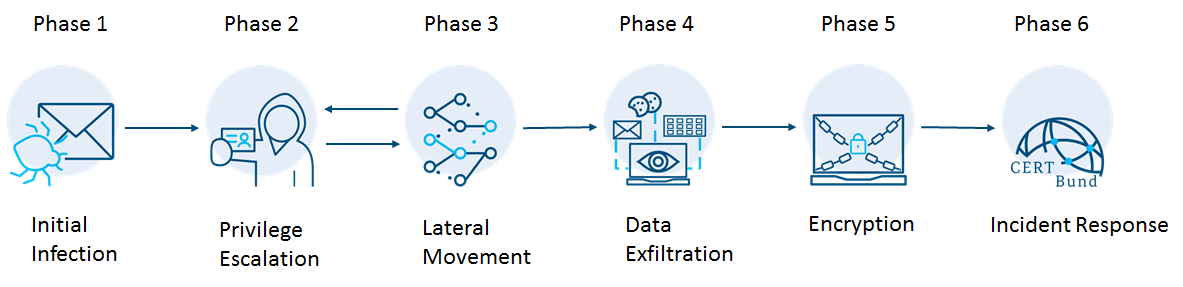
How can organizations protect themselves?
Keep your Asset Inventory up to date
Organizations should implement proactive measures to strengthen the organization’s Resilience. An essential element is an updated and complete inventory of assets. Only then will organizations have a chance to identify affected assets and isolate them in a timely manner.
Implement Awareness Training for employees
According to Verizon’s Data Breach Investigations Report (DBIR), stolen credentials and phishing emails are the top two ways ransomware finds its way into an organization. Desktop sharing software was involved in 40% of all breaches [3]. Training employees in regards to these Social Engineering patterns can raise the bar for threat actors significantly, not to mention locking down remote desktop and email protocols.
Harden your Assets
Ransomware infected systems via some kind of vulnerability in almost 10% of cases [3]. Often these vulnerabilities are already known and sometimes even fixed by the vendor. It is therefore crucial to keep all assets updated and patched. Remote access to assets (e.g. via VPN) should be limited to the bare minimum and especially secured (e.g. using 2-Factor-Authentication).
Keep 3-2-1 Backups
All personal data and business files should be part of a regular backup. The backup should be isolated from any network to prevent ransomware from infecting it. The 3-2-1 rule is best practice for implementing a backup strategy; keep three copies of information on two different storage media, and keep one of these media on another location.
Do not pay Ransom
In case an organization becomes victim of a ransomware attack, it is recommended to reach out to national information security authorities or law enforcement for help. The NCSC and FOIS, as well as ENISA, strongly advise against paying ransom [4,5].
Recommendation
Check if your organization is well prepared for ransomware:
- Is your asset inventory up to date?
- Do all assets have the latest security updates applied?
- Are your crown jewels backed up?
Need help gearing up for ransomware? Contact us for more information.
Sources
- [1] https://www.enisa.europa.eu/publications/enisa-threat-landscape-for-ransomware-attacks
- [2] BSI – Top 10 der Ransomware measures (bund.de)
- [3] Verizon DBIR
- [4] Encryption malware – What next? (admin.ch)
- [5] Umgang mit Lösegeldforderungen bei Angriffen mit Verschlüsselungstrojanern auf Kommunalverwaltungen (bund.de)
