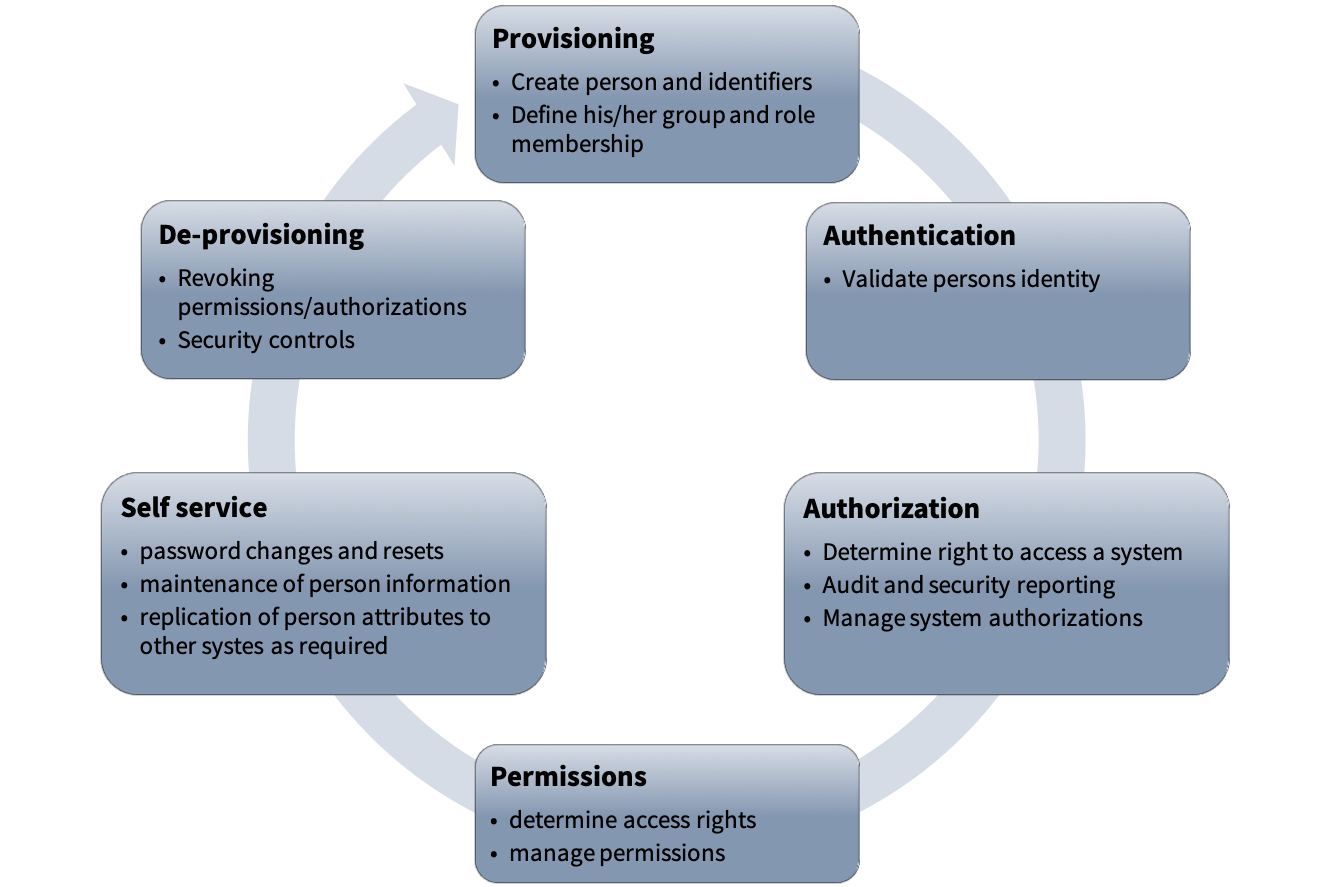
Identity and access management (IAM) is a wide field about defining and managing the roles and access privileges of individual network users and the circumstances in which users are granted (or denied) those privileges.
The core objective is to identify every individual as one digital identity. Once established, they must be monitored, maintained and modified throughout it’s access lifecycle. Some of the IAM tools needed are reporting and monitoring apps, password management tools, provisioning software, identity repositories and more. We help you to to meet the requirements of your organizations IT governance and regulatory compliance by providing the tools to implement comprehensive security, audit and access policies.
IAM Circle: