Losing company assets like laptops, smartphones, or documents, as well as assets getting stolen, are two well known risks to the Information Security of organizations. However, over the last years, Verizon’s Data Breach Investigation Report (DBIR) has shown a trend of data compromise being mainly confirmed in incidents of the latter kind [1].
The DBIR also highlights that the decrease in traveling and increase in home office in the period of 2020 – 2021 did not lead to a decrease in data breaches caused by these risks. Organizations should take this into account during their risk assessments and establish appropriate technical, physical, and logical measures against loss and theft.
Maintain an (IT) Asset Inventory
Since organizations can only protect what they know of, maintaining an up-to-date inventory of all (IT) assets is key. Asset inventories keep information of laptops, smartphones, etc. that belong to the organization. Information includes operating system version and patches, installed software, asset owner etc. In case an asset gets lost or stolen the inventory provides administrators with all relevant information to make quick decisions.
Asset inventories should be part of an asset management process. Asset management includes policies, procedures, and processes that help organizations account for all assets throughout their respective lifecycles [2].
Establish Mobile Device Management
Mobile Device Management (MDM) helps organizations secure and maintain assets in their infrastructure. It also allow administrators to update, configure, and govern assets remotely. If an IT asset goes missing, MDM solutions can remotely lock it, change the password, wipe all the corporate data contained within, or completely deactivate it in order to protect its data from unauthorized people.
Implement Access Control Policies
In order to keep unauthorized people from accessing data on a lost or stolen asset, state-of-the-art authorization measures should be set up. Organizations can make it harder for unauthorized people to get access by enforcing strong authentication; at least two authentication methods out of knowledge, ownership, and inherence are needed to gain access, for example, a Password and an Authenticator Pin.
Ideally access control policies are setup via the MDM uniformly across all devices.
Encrypt all Data
Encryption is a digital form of cryptography. It uses mathematical algorithms to scramble information so that only the person having the key (e.g., a password) is able to decode and access the information. Data on devices like laptops and smartphones should always be encrypted. This can be achieved by either encrypting individual files and folders, encrypting individual volumes or encrypting the whole disk. The latter method is the most transparent to employees, as it does not require them to save files to a special place on the disk. All files, folders, and volumes are automatically encrypted.
Ideally encryption is setup via the MDM uniformly across all devices.
Establish physical security
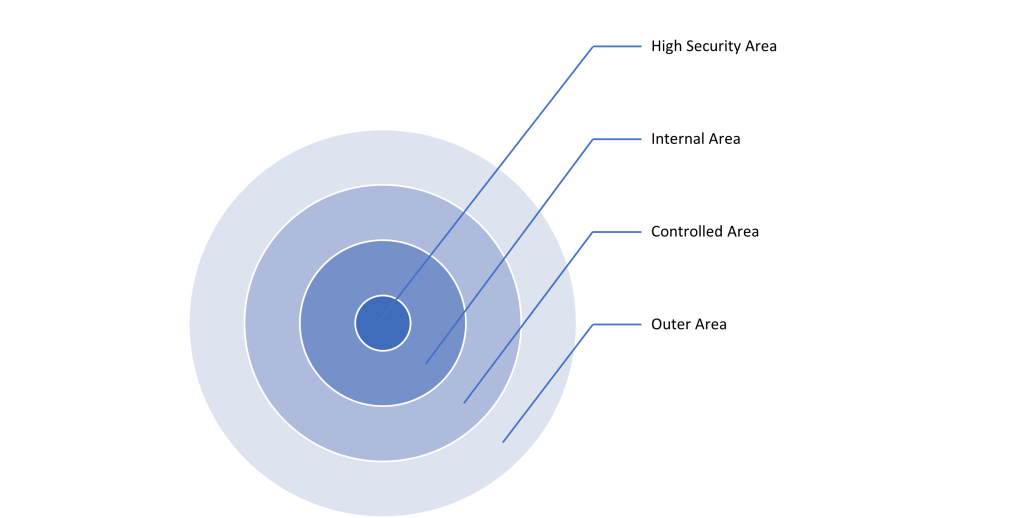
To lower the probability of assets getting stolen, organizations should establish an appropriate physical security concept with different security zones. An example zone concept could consist of a high security area, containing all assets with very high protection goals, an internal area where employee offices are located, a controlled area, for example, a lobby, and an outer area. It is important that each zone implements a different access control measure so that a person cannot get through more than one zone in one step.
Train your employees
Awareness campaigns for employees should include proper mobile device and physical security policies and regulations. They should know their responsibilities, for example, not to leave laptops and mobile phones unattended, who to contact in case of a lost or stolen asset, and to watch out for people tailgating.
Recommendation
Check if your organization is well prepared for lost and stolen assets:
- Is your asset inventory complete and up to date?
- Is a Mobile Device Management solution in place that rolls out access control and encryption via policy to all devices?
- Does your zone concept follow information security best practices?
Need help mitigating the risk of lost and stolen devices for your organization? Contact us for more information.
Sources
- [1] Verizon DBIR
- [2] https://www.ncsc.gov.uk/blog-post/asset-management-for-cyber-security
