Information and supporting processes, systems and networks are of crucial business value and most of the time mission critical. The main security goals to achieve for business critical data and services are confidentiality, integrity and availability, which contribute significantly to competitive advantage, liquidity, rentability, legal compliance and reputation.
Information security protects information from a magnitude of threats. It should ensure maintenance of business operations, surpress business harming influence and maximize investment rentability and business opportunities.
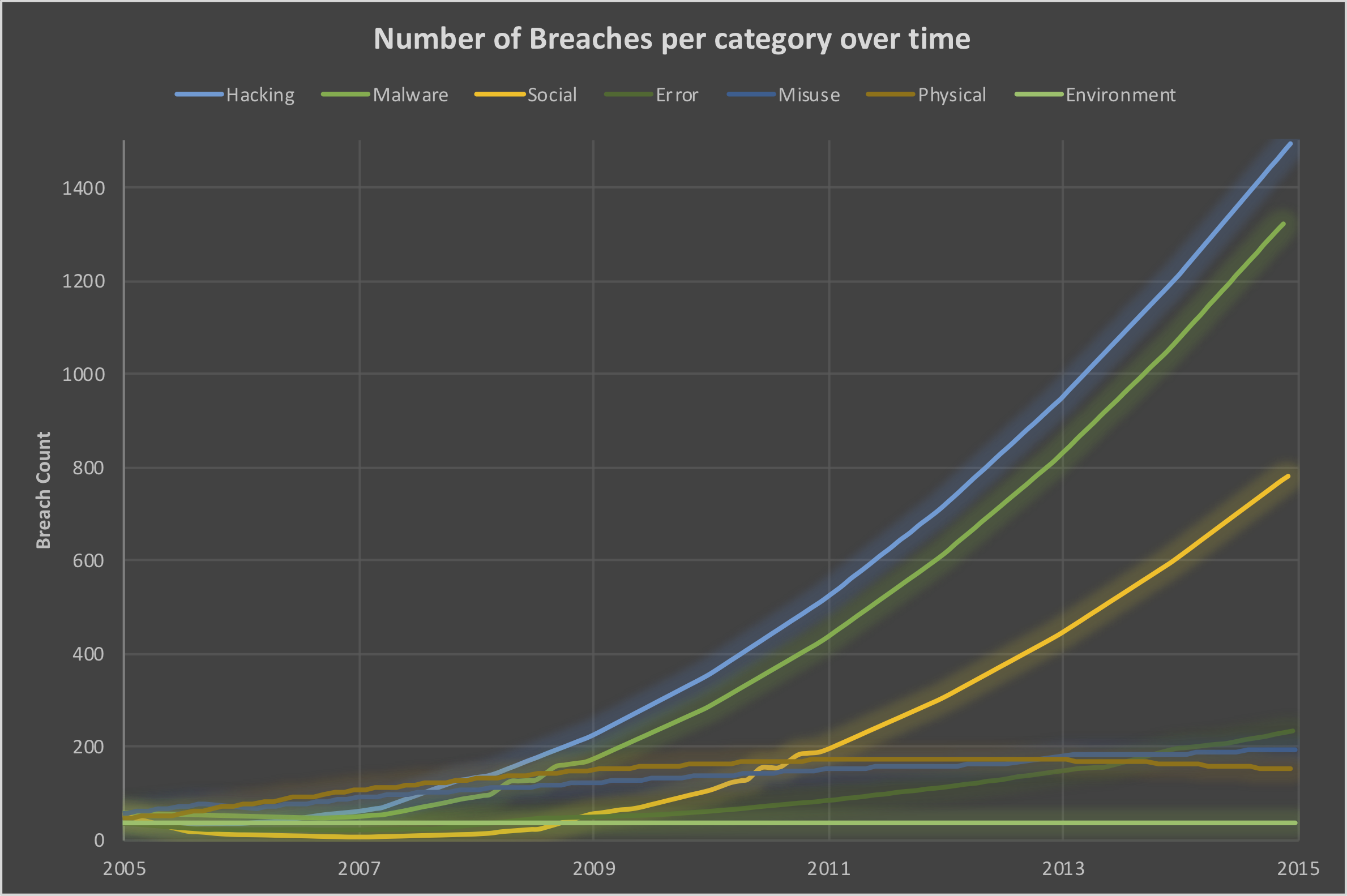
During the last decades the number of reported (cyber) breaches increased dramatically, which is not only caused by more and better detection and reporting, but also due to the increased number of systems and applications connected to the internet, which results in a larger attack surface.
Figure 1 demonstrats this increase impressively. Hacking, Malware and Social (see Section Threat Categories below for definitions) are on the rise, while the physical category has a downward trend. An explaination could be that direct (physical) access to systems is no longer required to exfiltrate data and network and/or internet access is sufficient.
Threat Categories
Data breaches can occur in multiple ways and there are several threat catalogues and definitions out there. They have the more or less the following basis in common:
- Hacking: Any attempt to compromise a victims security goals, such as confidentiality, integrity and availability by bypassing security measures.
- Malware: Any code or software programmed to compromise a victims security goals, such as confidentiality, integrity and availability.
- Social: All activities requiring human interaction, such as trying to steal someones password.
- Physical: All activities where threat actors have physical access to systems that contain business critical data or are critical for business operations.
- Misuse: Mostly related to insider threats, where someone with appropriate access right is misusing these to harm the firm’s security goals.
- Error: Simple errors and mistakes that result in confidentiality, integrity and availability violations.
Rising external Requirements
Defending business data and services against adversaries seems not to be challenging enough though, the number of external driven requirements are constantly raising.
The following listing is not meant to be complete, but should be capable to provide some insight in the ever growing list of external requirements to be satisfied.
1980s
1990s
2000s
- NIST
- PIPEDA (Canada)
- USA Patriot Act
- EC 8th Directive
- PCI
- EC Data Privacy
- FISMA I and II
- CA SB 1386
- NERC CIP
- SOX
- Basel II Accord
- National Credit Union Administration
2010s
One should be aware that being compliant with regulatory or legal requirements does not necessarily imply a sufficient risk mitigation, nor does a sufficient risk mitigation imply sufficient compliance.
This topic will be discussed further in another article.
The myth of 100% protection
Given the rising complexity of the IT stacks and the fact that data needs to be consumable by humans in the very end bears an intrinsic non vanishing risk of being exploited by adversaries.
The following quote summarizes this fact aptly:
Given enough time, resources and inclination, criminals can breach virtually any single organization they choose but do not have adequate resources to breach all organizations.
(Verizon Data Breach Investigations Report 2010)
